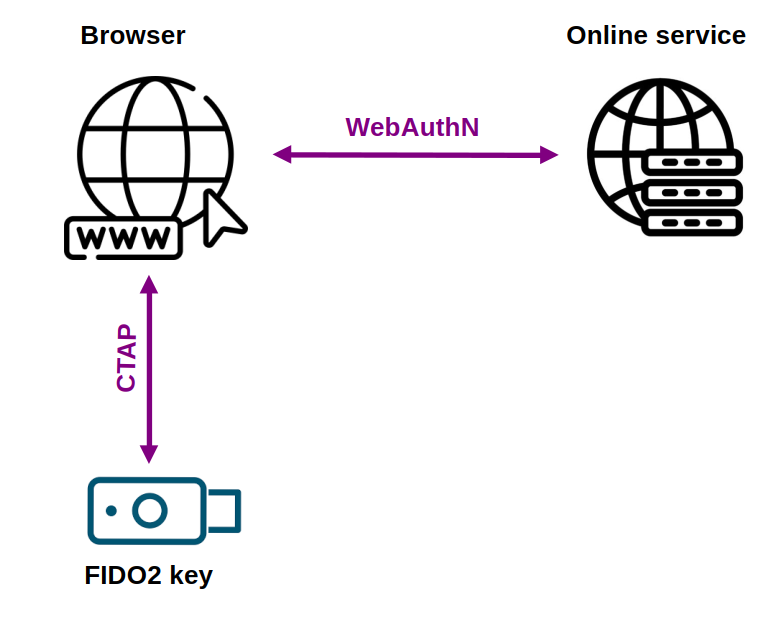
FIDO2 is an authentication standard developed by the FIDO Alliance, based on the principle of public key cryptography. The goal of FIDO2 is to replace the use of passwords for authentication, limiting the risks of password theft through phishing. To achieve this, FIDO2 uses Passkeys, which are digital credentials that can be stored on physical security keys.


FIDO2 is based on the Client To Authenticator Protocol (CTAP), which defines the communication between the browser and the FIDO2 key, and the Web Authentication API (WebAuthN), which allows servers to register and authenticate users using public-key cryptography instead of a password.
To understand the FIDO2 authentication mechanism, you need to know the principle of public key cryptography. So I propose a brief reminder of this principle used for data encryption and digital signature.
Reminder of the principle of public key cryptography
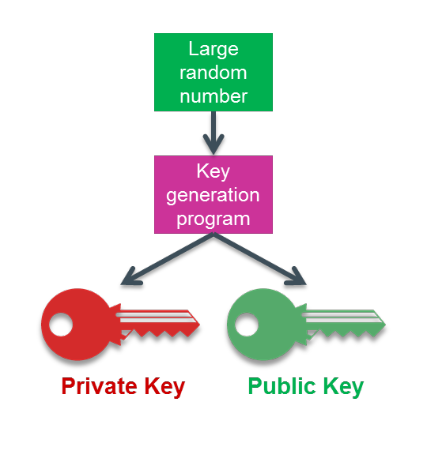
The principle of public key cryptography is based on a pair of mathematically related cryptographic keys. A key generation program generates these two keys from a random number. The public key can be made available to everyone, while the private key must remain confidential and kept safe by its owner.
Anything encrypted with a public key can only be decrypted by its corresponding private key and vice versa. The key pair is used to ensure the confidentiality of data (encryption) and guarantee its authenticity (digital signature).
Using Public Key Cryptography for Data Encryption
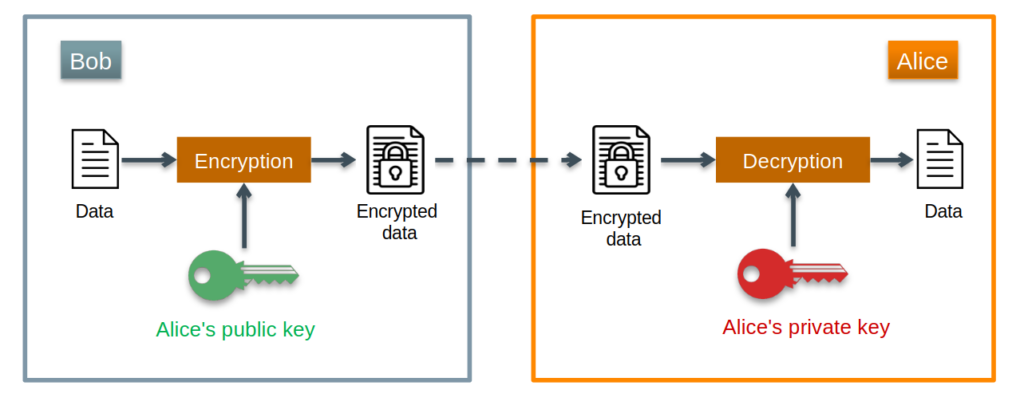
In the example below, Bob wants to send a confidential document to Alice, and that no one but Alice can decrypt it. Bob then encrypts the document with Alice’s public key (this key being public, everyone can know it, it can be distributed in a directory for example). Only Alice can decrypt the document using her private key. Alice does not need to know Bob’s public key in this mechanism.
Using Public Key Cryptography for Digital Signature
In the example below, Alice wants to make sure that the document she receives was indeed sent by Bob and that it was not modified during its transport. To do this, Bob will sign his document and send Alice the document accompanied by his digital signature. The signature corresponds to the encryption of the cryptographic hash of the document with Bob’s private key.
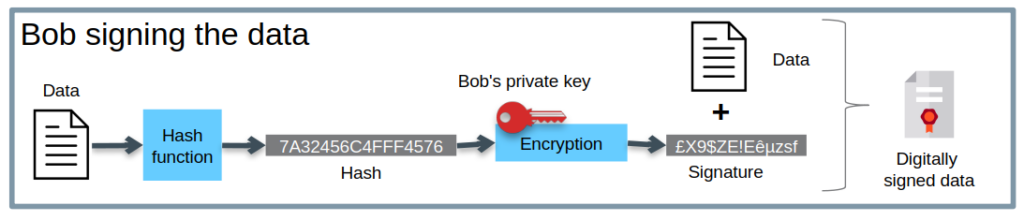
When Alice receives the message, she decrypts the signature with Bob’s public key. She therefore obtains the cryptographic hash of the original document. She simply has to verify that this cryptographic hash gives a result identical to that of the document she has just received. If the results are identical, this proves that the sender is indeed Bob and that the document received is indeed identical to the original.
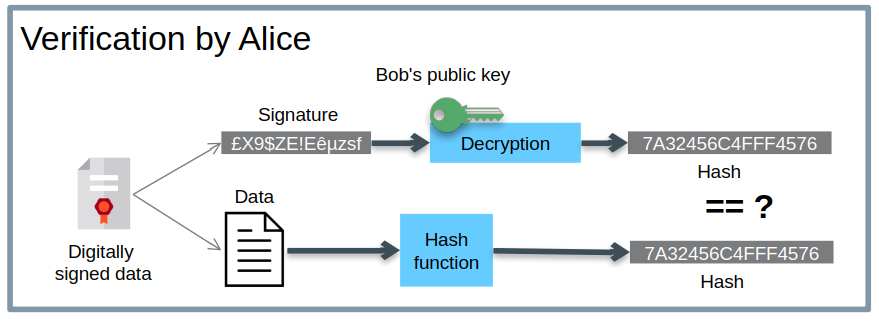
Digital signature ensures authentication and data integrity.
Enrolling a FIDO2 key
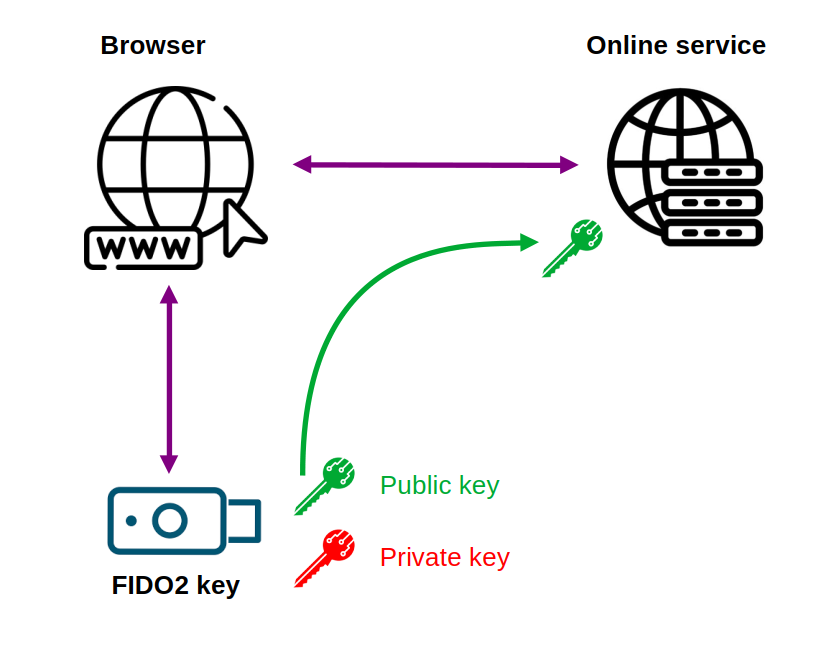
The first step is to enroll the Passkey with the service you want to use it to authenticate with. During this registration process, the security key creates a unique public/private key pair for that service and the user account. The private key is stored on the security key and must never leave it. The public key is transmitted to the online service and associated with the user account.
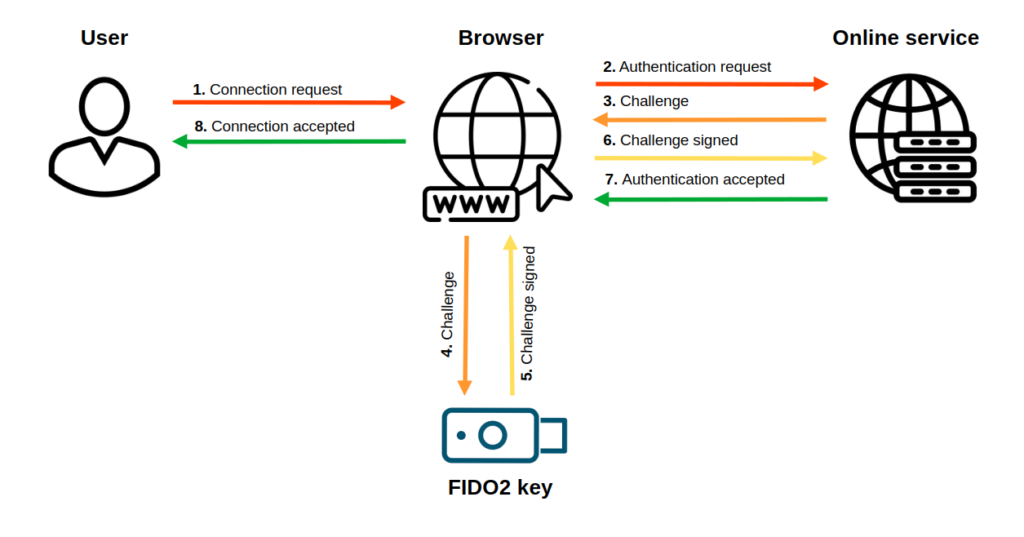
Login with a FIDO2 key
Once the security key is enrolled with the service, the user can log in to it with their Passkey. The service sends a challenge to the security key. The security key signs this challenge with its private key and returns this signed challenge to the service. The service can then verify this signature using the public key associated with the user account during enrollment. If the verification is successful, the user is logged in to the service.
The principle of USB security keys is generally to insert the key into a USB port of the computer, and to touch the key to confirm the connection to the service. Indeed, the FIDO standard requires a gesture from the user in order to confirm his presence during authentication.


Strong Authentication vs Multi-Factor Authentication?
It is important to distinguish between strong authentication and multi-factor authentication. Strong authentication is authentication based on a cryptographic protocol that is resistant to attacks. Multi-factor authentication is authentication based on at least 2 authentication factors.
FIDO2 is based on a strong cryptographic protocol and allows the use of multiple authentication factors. Having the security key is a possession factor, and adding a PIN code is a knowledge factor. FIDO2 is a strong and multi-factor authentication standard.
To go further, I strongly recommend that you read the ANSSI (National Agency for Information Systems Security) guide: Recommendations relating to multi-factor authentication and passwords.
Use as an additional authentication factor
Some sites do not allow to log in only with a FIDO2 key, but they allow to use it as an additional authentication factor to the password.
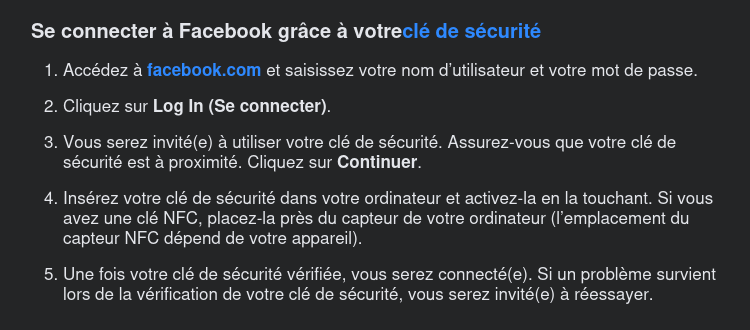
For example, to this day the Facebook site still requires the use of the password, the FIDO2 key only serves as an additional authentication factor.
Testing your security key
If you have a FIDO2 security key, you can test it now using the website https://www.token2.com/tools/fido2-demo.
- Insert the security key into a USB port
- Click on Register
- Enter the security key PIN code (if you selected the option)
- Touch the security key
If everything went well, your key is now enrolled in the FIDO2 demo service at www.token2.com.
You can now log in to this service with your security key.
- Click Login
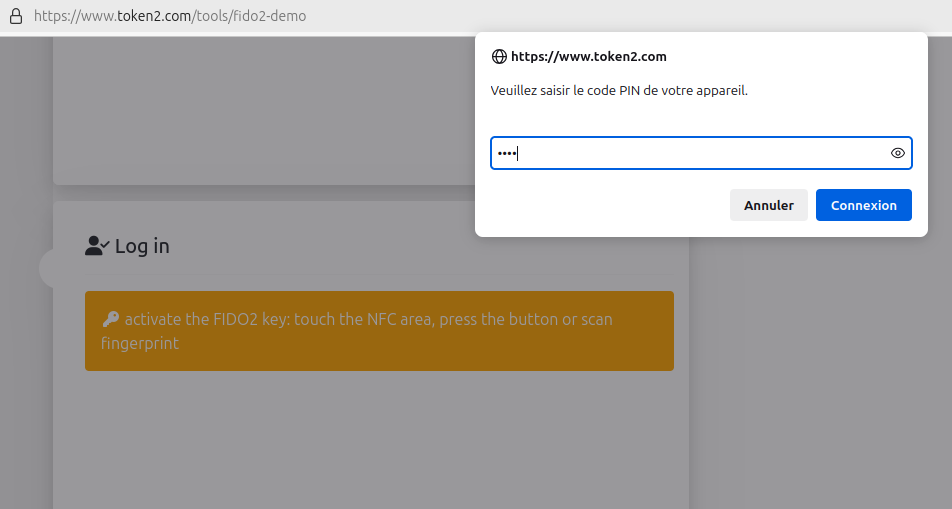
- Enter the security key PIN (if you selected the option)
- Touch the security key
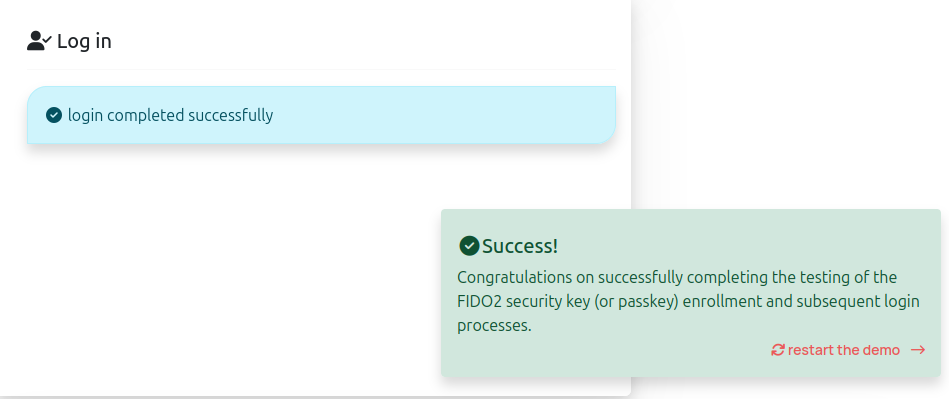
Congratulations, you have just successfully connected to an online service for the first time using a FIDO2 security key. 🙂
A FIDO 2 security key on a Raspberry Pi Pico?
Pol Henarejos’ Pico FIDO project lets you turn your Raspberry Pi Pico into a FIDO access key.
Download the latest firmware version corresponding to your hardware (pico_fido_pico-5.12.uf2 for example for a Raspberry Pi Pico) from the Releases area.
To install this firmware on the Pico, you must start the Pico in Bootloader mode. To do this, hold down the BOOTSEL button and connect the Pico to your PC via a USB cable. Do not release the button until Pico is properly connected to your PC. The Pico is then seen as a USB mass storage named RPI-RP2 containing the INDEX.HTML and INFO_U2F.TXT files. Simply drag and drop the UF2 file onto this mass storage.
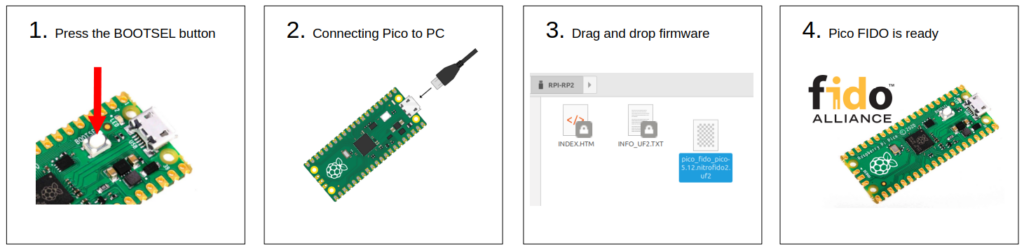
When it reboots, the Pico LED starts blinking, it now behaves like a FIDO2 key. The BOOTSEL button simply serves as a button to press when the browser asks to “touch the key” during the enrollment or login procedure.
Note: As of the date of writing this article (October 4, 2024), I have spotted a few bugs. Pico FIDO does not work with the Firefox browser on my Linux system (Pico FIDO 5.12, Firefox 131.0), however it works fine under Chromium. The procedure for enrolling a Pico FIDO key does not seem to work for the Github site.
Example of authentication to the Linkedin.com site with a Pico FIDO key
The Linkedin.com site allows you to connect with a FIDO2 key, we will test the enrollment of our Pico FIDO key on this website:
Step 1: Once connected to the site, go to the Identification and security menu and click on Access keys
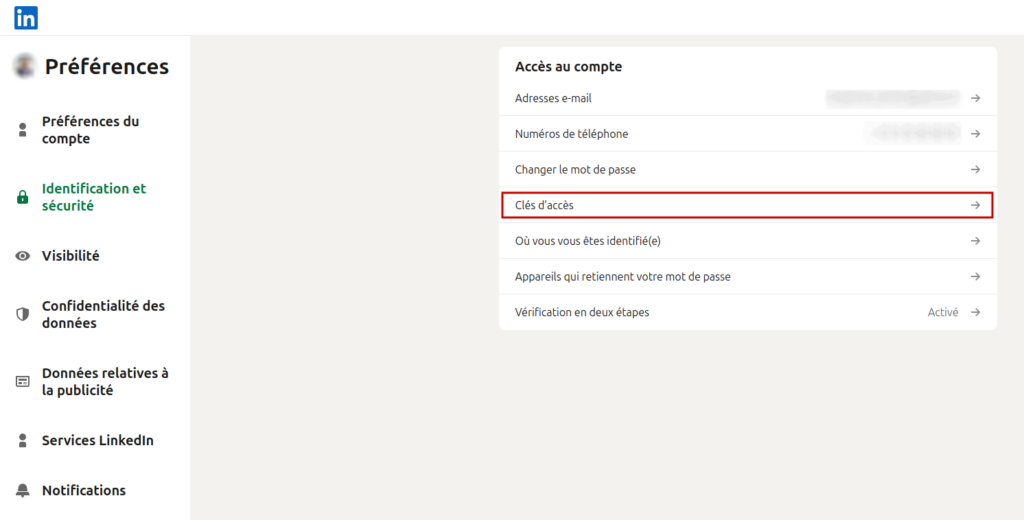
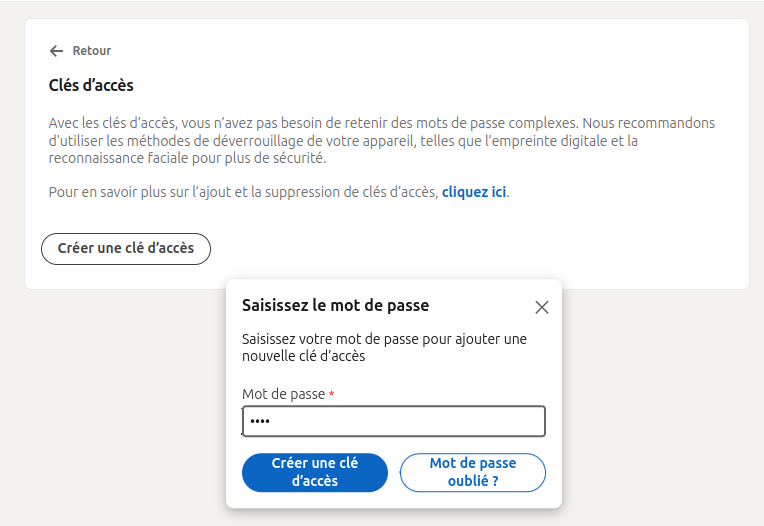
Step 2: Click on Create an access key and enter the password of your Linkedin account
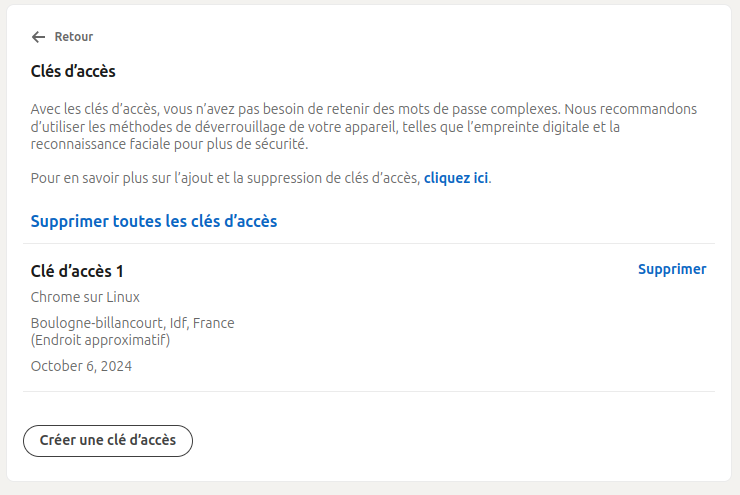
Step 3: As with any key enrollment, enter your PIN code and tap the key. Your key now appears in the list of authorized access keys to authenticate on Linkedin.
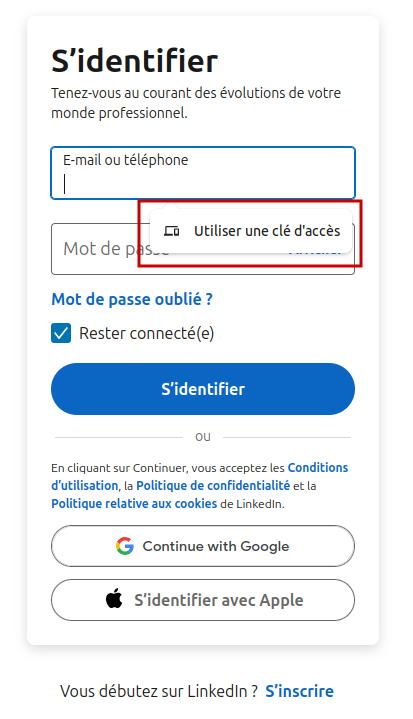
Step 4: You can now log in to Linkedin with your security key, by clicking on the Email or phone area the Use an access key option appears. Just click on it, type the PIN code and touch the key to be connected to Linkedin.
Important note regarding the security of a FIDO2 key on a Raspberry Pi Pico
Warning, using a Pico as a FIDO2 security key is risky. Indeed, the private key is not stored securely in a Pico because its flash memory is not protected. It is therefore possible to duplicate the FIDO2 key or extract the secrets (PIN code and private keys) from its flash memory.
This is why it is strongly recommended to use a security key (Winkeo-C FIDO2 for example) that includes a security component that protects the information stored in the key.
Conclusion
Using a FIDO2 key both simplifies authentication to online services and improves the level of security. Indeed, FIDO 2 is a strong multifactor authentication and effectively combats password theft.
I recommend reading issue 56 of Hackable magazine published in September 2024, an entire article is dedicated to this subject.
I hope you found this article interesting. Feel free to give your opinion by clicking on the stars below.

